FluBot is akin to most scams and hacks common on the internet today, and it particularly threatens android users. Here’s what you need to know about FluBot, and what you could do to keep your data secured.
About FluBot
FluBot is a malware that first reared its head in early 2021, it has its origins traced to Spain and then travelled through the UK and then many parts of Europe. It thrives on its victims’ smartphones. It takes the guise of an official alert from a delivery company by sending them an SMS notification, intimating them on a package that will be arriving, and encourages them to further tap on a URL to track it.
Once, the victim does that, the URL opens up a new page that instructs the user to download a tracking app to await the package. The supposed tracking app to the users earnest dismay turns out to be a malware, the FluBot malware is quite devious, it keep tabs on the user’s smartphone activity and like many other scam, hacks and internet fraudulent activities the aim, is to steal financial login information so your bank accounts becomes vulnerable and under hackers attack.
FluBot newest Tactics
Hackers are usaully experimentalists, they lack professionalism and thrive on luck and coincidence but their schemes should not be underrated. Becoming a frequent report most affected victims had the authorities on top of the situation, especially in the FluBot’s targeted countries, creating more awareness to citizens about Flubot, and exposing the nature of their SMS that usually trick users into the downloading their worst nightmare.
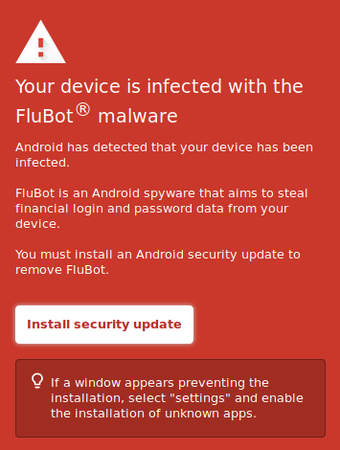
So, FluBot hackers havin been found out, wouldn’t take a defeat yeah? They evolved, and came out with newer tactics and trickery. The hackers seem to now draw the world’s eyes to FluBot. So, when you receive their text messages and perhaps proceed to tap on the URL link, they save you the stress of thinking they are operating undercover they directly issue a pop-up warning to their victims that their phones are infected with FluBot and that the only way to get it out, according to FluBot, is to download an “Android security update.” Again that is an even much bigger deceit, since (The “Android security update” is equally infected with FluBot.)
Alternatively this pop-up may come as a warning that you have a special voicemail that you can only listen to via a particular app. These schemes are spreading worldwide; CERT NZ, New Zealand’s Computer Emergency Response Team, recently put out an excellent blog post on the subject for its citizens, and it applies to anyone who might encounter the FluBot scam.
How to prevent FluBot from infecting your android smartphone
First, completely resist the urge to click on these links: Generally, do not click on strange links especially ones asking you to track a package you know very well you never ordered ( I would say that’s greed). Be certain to always verify the legitimacy of a link before opening it, on any device, a smartphone, your computer, or any gadget, be cybersecurity consious.
Another effective measure is to set up your Android phone in such a way that apps are not able to install additional unknown apps without your permission. That will prevent apps like FluBot from sneaking their way onto your device.
For Android 8 or later, go-to Settings > Apps > Special access > Install unknown apps, then make sure “Not allowed” is set for your apps. If any app says “Allowed,” switch it to “Not allowed.” For Android 7 or earlier, tap on Settings > Security (or Lockscreen and Security), and ensure “Unknown sources” is disabled.
If you had ignorantly tapped the link in the text message, but hadn’t downloaded any apps adviced, the good news is you may not be at risk at this stage. As it looks, so far, FluBot is only effective once you actually download the app tied to the link in the pop-up; the link in the SMS just takes you to the pop-up, so that process alone shouldn’t infect your phone with the malware. Still, CERT NZ recommends you change your passwords if you did tap on that SMS link, just to be on the safe side.
And OK, let’s say you did select the link in the pop-up, and you downloaded the hidden FluBot app within it. Simply, Factory reset your phone to completely delete any trace of FluBot on your device, or restore from a backup from before you downloaded the FluBot app. Then change all of the passwords for your connected accounts. You may also want to contact your bank to make sure there has been no suspicious activity on your account and never again click or tap on any unexpected links.
Is FLUBOT only effective on Android Phones?
Unfortunately, the answer is YES, iPhones are exempted though they can receive the message and open the pop-up, but the app cannot be installed on iOS.
